Nyroxis Endpoint SIEM
• Correlation-driven detection and real-time alerting
• Behavioral indicators for anomalous and malicious activity
• Encrypted event storage with integrity and tamper resistance
• Forensic-ready evidence collection and retention
• Designed for minimal noise and operational clarity
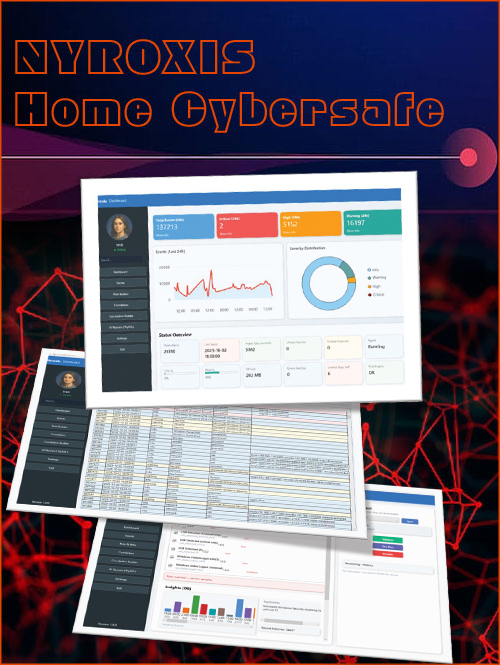
About Nyroxis SIEM
Traditional antivirus solutions focus on detecting and removing known malicious files. They typically react after an infection has already occurred and provide little visibility into how an attacker gained access or what actions were taken inside the system.
Nyroxis takes a different approach. As an endpoint-focused SIEM, it continuously monitors system activity, correlates events, and analyzes behavior across processes, networks, and user actions. When suspicious activity is detected, Nyroxis does not simply terminate the event. Instead, it observes, records, and correlates attacker behavior within a controlled monitoring scope, identifying tactics and preserving forensic evidence.
The result is not only prevention, but visibility and accountability — allowing security, legal, and investigative teams to understand what happened, how it happened, and respond with confidence.
Stay ahead of threats with Nyroxis
Real-Time Threat Monitoring
Continuous surveillance of your digital environment, detecting suspicious activities the moment they occur.
No delays, no missed alerts.
Smart Intrusion Traps
Unlike traditional defenses that just block, Nyroxis engages attackers in a controlled trap.
mapping their moves, identifying tactics, and gathering evidence.
Actionable Intelligence
Turn raw data into clear, actionable insights so you can respond faster and smarter, staying ahead in the cyber battlefield.
If you or a family member handle sensitive information and operate beyond the scope of ordinary individuals.

Your Next-Level Cyber Defense
Absolute Cyber Vigilance
Nyroxis is a local, silent SIEM system designed for complete monitoring of system activities. It logs and analyzes all suspicious events without interfering with system performance — ideal for high-risk environments and sensitive roles where accurate evidence collection is critical.
--- FIVE CORE MODULES ---
Network Activity Tracking
Process Monitoring
Critical File Integrity Checks
USB & Registry Activity Tracking
Suspicious Event Correlation Engine

Advanced Security Challenges
With customizable alert rules, Nyroxis allows you to instantly detect targeted threats. From monitoring dangerous keywords in PowerShell to spotting unusual USB activity, everything is logged and analyzed in real time.
--- FIVE INTELLIGENT FEATURES ---
Advanced log filtering and search
Multi-level alerts (Critical, Warning, Info)
Multilingual interface (FR/EN/DE)
CSV/JSON export for external analysis
Database optimization and maintenance

New Era, New Defense
Step into the new era of cybersecurity with Nyroxis. Operating silently, fully offline, and without any central server dependency, it ensures security in any environment. From hidden honeypots to legally admissible evidence collection — all in one lightweight, intelligent solution.
--- FIVE STERATEGIC ADVANTAGES ---
No alerting the attacker (Stealth Mode)
Timestamped, legally valid evidence collection
Fully offline operation
Compatibility with sensitive environments
Future integration with central SIEM

Professional Achievements
Incidents That Could Have Been Prevented with Nyroxis
LastPass Breach (2022)
In 2022, attackers compromised the personal home computer of a senior DevOps engineer at LastPass. By installing malware, they gained access to sensitive company vaults stored in the cloud. If Nyroxis had been installed on that home device: Suspicious PowerShell executions and unusual network activity could have been detected and alerted before the breach escalated.
Colonial Pipeline Ransomware Attack 2021
Hackers gained entry to Colonial Pipeline’s network by using login credentials stored on an employee’s personal device. This led to the shutdown of the largest fuel pipeline in the United States for several days. If Nyroxis had been on the employee’s home computer: Unusual VPN connections and abnormal login attempts would have been flagged instantly.
SolarWinds Supply Chain Attack 2020
In this major supply chain attack, intruders first breached personal systems used by some SolarWinds staff. They then inserted malicious code into an official software update, which was distributed to thousands of organizations. If Nyroxis had been installed on those personal systems: Unauthorized executable transfers and suspicious system modifications could have been detected early.
Target Data Breach 2013
Attackers infiltrated Target’s network through a third-party contractor’s personal computer, which was used to connect remotely to the company. This resulted in the theft of millions of customers’ credit card records. If Nyroxis had been on the contractor’s system: Unauthorized network connections and unusual traffic patterns would have triggered alerts before the intrusion succeeded.
Nyroxis Security Plans
Secure your personal and work devices with our advanced offline security monitoring system
Whether you’re an individual, a family member of a sensitive role, or part of a high-security environment, Nyroxis keeps you protected without alerting attackers.
FREE PLAN – Community Edition (Windows)
For personal use & open-source community testingGithub version
ENTERPRISE PLAN – Pro Edition (Multi-Platform)
Full feature set for professionals, VIPs, high-security environmentsContact Us
My Blog
GootLoader Malware Uses 500–1,000 Concatenated ZIP Archives to Evade Detection
The JavaScript (aka JScript) malware loader called GootLoader has been observed using a malformed ZIP archive that’s designed to sidestep detection efforts by concatenating anywhere from 500 to 1,000 archives.
“The actor creates a malformed archive as an anti-analysis technique,” Expel security researcher Aaron Walton said in a report shared with The Hacker News. “That is, many unarchiving tools

Five Malicious Chrome Extensions Impersonate Workday and NetSuite to Hijack Accounts
Cybersecurity researchers have discovered five new malicious Google Chrome web browser extensions that masquerade as human resources (HR) and enterprise resource planning (ERP) platforms like Workday, NetSuite, and SuccessFactors to take control of victim accounts.
“The extensions work in concert to steal authentication tokens, block incident response capabilities, and enable complete account

Your Digital Footprint Can Lead Right to Your Front Door
You lock your doors at night. You avoid sketchy phone calls. You’re careful about what you post on social media.
But what about the information about you that’s already out there—without your permission?
Your name. Home address. Phone number. Past jobs. Family members. Old usernames.
It’s all still online, and it’s a lot easier to find than you think.
The hidden safety threat lurking online
Most
LOTUSLITE Backdoor Targets U.S. Policy Entities Using Venezuela-Themed Spear Phishing
Security experts have disclosed details of a new campaign that has targeted U.S. government and policy entities using politically themed lures to deliver a backdoor known as LOTUSLITE.
The targeted malware campaign leverages decoys related to the recent geopolitical developments between the U.S. and Venezuela to distribute a ZIP archive (“US now deciding what’s next for Venezuela.zip”)

China-Linked APT Exploited Sitecore Zero-Day in Critical Infrastructure Intrusions
A threat actor likely aligned with China has been observed targeting critical infrastructure sectors in North America since at least last year.
Cisco Talos, which is tracking the activity under the name UAT-8837, assessed it to be a China-nexus advanced persistent threat (APT) actor with medium confidence based on tactical overlaps with other campaigns mounted by threat actors from the region.
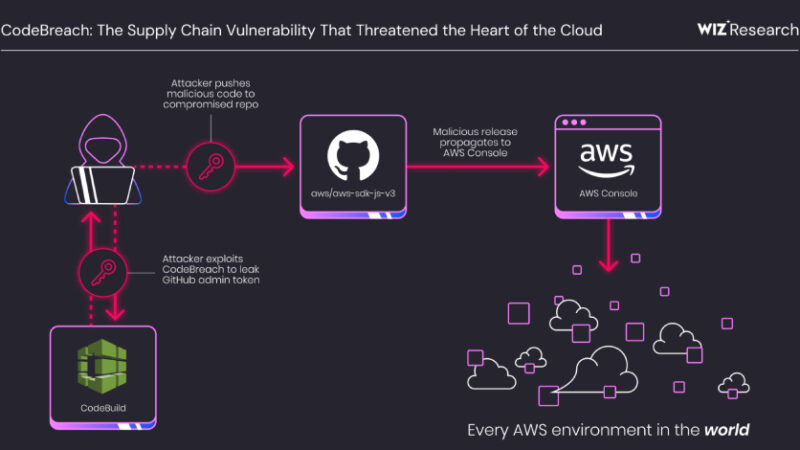
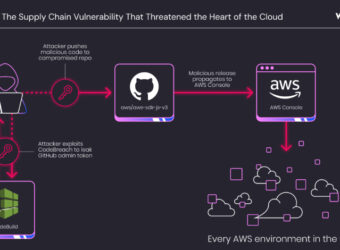
AWS CodeBuild Misconfiguration Exposed GitHub Repos to Potential Supply Chain Attacks
A critical misconfiguration in Amazon Web Services (AWS) CodeBuild could have allowed complete takeover of the cloud service provider’s own GitHub repositories, including its AWS JavaScript SDK, putting every AWS environment at risk.
The vulnerability has been codenamed CodeBreach by cloud security company Wiz. The issue was fixed by AWS in September 2025 following responsible disclosure on