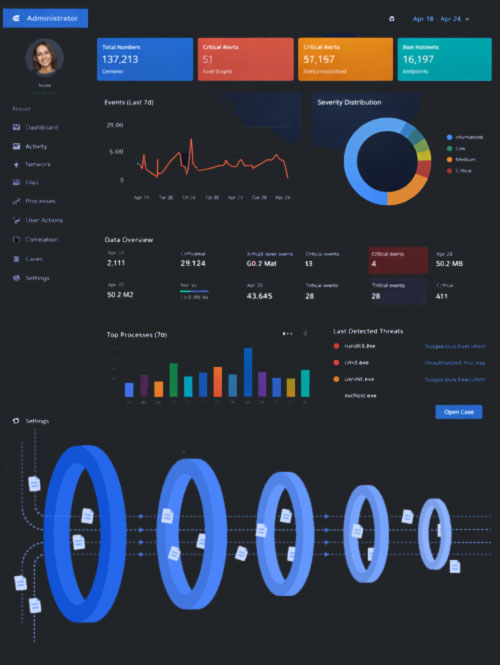
Nyroxis Endpoint SIEM
• Correlation-driven detection and real-time alerting
• Behavioral indicators for anomalous and malicious activity
• Encrypted event storage with integrity and tamper resistance
• Forensic-ready evidence collection and retention
• Designed for minimal noise and operational clarity
About Nyroxis SIEM
Traditional antivirus solutions focus on detecting and removing known malicious files. They typically react only after compromise has occurred and provide limited visibility into how attackers gained access or what actions they performed inside the system.
Nyroxis takes a different approach. As an endpoint-focused SIEM, it continuously monitors system activity, correlates events, and analyzes behavior across processes, networks, and user actions in real time.
When suspicious activity is detected, Nyroxis does not simply terminate the event. Instead, it observes, records, and correlates attacker behavior within a controlled monitoring scope, identifying tactics and preserving forensic evidence.
The result is more than prevention. Nyroxis delivers visibility, traceability, and accountability. enabling security, legal, and investigative teams to understand exactly what happened, how it happened, and respond with confidence.
Stay ahead of threats with Nyroxis
Real-Time Threat Monitoring
Continuous surveillance of your digital environment, detecting suspicious activities the moment they occur.
No delays, no missed alerts.
Smart Intrusion Traps
Unlike traditional defenses that just block, Nyroxis engages attackers in a controlled trap.
mapping their moves, identifying tactics, and gathering evidence.
Actionable Intelligence
Turn raw data into clear, actionable insights so you can respond faster and smarter, staying ahead in the cyber battlefield.
If you or a family member handle sensitive information and operate beyond the scope of ordinary individuals.

Your Next-Level Cyber Defense
Absolute Cyber Vigilance
Nyroxis is a local, silent SIEM system designed for complete monitoring of system activities. It logs and analyzes all suspicious events without interfering with system performance — ideal for high-risk environments and sensitive roles where accurate evidence collection is critical.
--- FIVE CORE MODULES ---
Network Activity Tracking
Process Monitoring
Critical File Integrity Checks
USB & Registry Activity Tracking
Suspicious Event Correlation Engine

Advanced Security Challenges
With customizable alert rules, Nyroxis allows you to instantly detect targeted threats. From monitoring dangerous keywords in PowerShell to spotting unusual USB activity, everything is logged and analyzed in real time.
--- FIVE INTELLIGENT FEATURES ---
Advanced log filtering and search
Multi-level alerts (Critical, Warning, Info)
Multilingual interface (FR/EN/DE)
CSV/JSON export for external analysis
Database optimization and maintenance

New Era, New Defense
Step into the new era of cybersecurity with Nyroxis. Operating silently, fully offline, and without any central server dependency, it ensures security in any environment. From hidden honeypots to legally admissible evidence collection — all in one lightweight, intelligent solution.
--- FIVE STERATEGIC ADVANTAGES ---
No alerting the attacker (Stealth Mode)
Timestamped, legally valid evidence collection
Fully offline operation
Compatibility with sensitive environments
Future integration with central SIEM

Professional Achievements
Incidents That Could Have Been Prevented with Nyroxis
LastPass Breach (2022)
In 2022, attackers compromised the personal home computer of a senior DevOps engineer at LastPass. By installing malware, they gained access to sensitive company vaults stored in the cloud. If Nyroxis had been installed on that home device: Suspicious PowerShell executions and unusual network activity could have been detected and alerted before the breach escalated.
Colonial Pipeline Ransomware Attack 2021
Hackers gained entry to Colonial Pipeline’s network by using login credentials stored on an employee’s personal device. This led to the shutdown of the largest fuel pipeline in the United States for several days. If Nyroxis had been on the employee’s home computer: Unusual VPN connections and abnormal login attempts would have been flagged instantly.
SolarWinds Supply Chain Attack 2020
In this major supply chain attack, intruders first breached personal systems used by some SolarWinds staff. They then inserted malicious code into an official software update, which was distributed to thousands of organizations. If Nyroxis had been installed on those personal systems: Unauthorized executable transfers and suspicious system modifications could have been detected early.
Target Data Breach 2013
Attackers infiltrated Target’s network through a third-party contractor’s personal computer, which was used to connect remotely to the company. This resulted in the theft of millions of customers’ credit card records. If Nyroxis had been on the contractor’s system: Unauthorized network connections and unusual traffic patterns would have triggered alerts before the intrusion succeeded.
Nyroxis Security Plans
Secure your personal and work devices with our advanced offline security monitoring system
Whether you’re an individual, a family member of a sensitive role, or part of a high-security environment, Nyroxis keeps you protected without alerting attackers.
FREE PLAN – Community Edition (Windows)
For personal use & open-source community testingGithub version
ENTERPRISE PLAN – Pro Edition (Multi-Platform)
Full feature set for professionals, VIPs, high-security environmentsContact Us
My Blog
Malicious npm Package Posing as OpenClaw Installer Deploys RAT, Steals macOS Credentials
Cybersecurity researchers have discovered a malicious npm package that masquerades as an OpenClaw installer to deploy a remote access trojan (RAT) and steal sensitive data from compromised hosts.
The package, named “@openclaw-ai/openclawai,” was uploaded to the registry by a user named “openclaw-ai” on March 3, 2026. It has been downloaded 178 times to date. The library is still available for

UNC4899 Breached Crypto Firm After Developer AirDropped Trojanized File to Work Device
The North Korean threat actor known as UNC4899 is suspected to be behind a sophisticated cloud compromise campaign targeting a cryptocurrency organization in 2025 to steal millions of dollars in cryptocurrency.
The activity has been attributed with moderate confidence to the state-sponsored adversary, which is also tracked under the cryptonyms Jade Sleet, PUKCHONG, Slow Pisces, and

⚡ Weekly Recap: Qualcomm 0-Day, iOS Exploit Chains, AirSnitch Attack & Vibe-Coded Malware
Another week in cybersecurity. Another week of “you’ve got to be kidding me.”
Attackers were busy. Defenders were busy. And somewhere in the middle, a whole lot of people had a very bad Monday morning. That’s kind of just how it goes now.
The good news? There were some actual wins this week. Real ones. The kind where the good guys showed up, did the work, and made a dent. It doesn’t always

Can the Security Platform Finally Deliver for the Mid-Market?
Mid-market organizations are constantly striving to achieve security levels on a par with their enterprise peers. With heightened awareness of supply chain attacks, your customers and business partners are defining the security level you must meet.
What if you could be the enabler for your organization to remain competitive — and help win business — by easily demonstrating that you meet these

Chrome Extension Turns Malicious After Ownership Transfer, Enabling Code Injection and Data Theft
Two Google Chrome extensions have turned malicious after what appears to be a case of ownership transfer, offering attackers a way to push malware to downstream customers, inject arbitrary code, and harvest sensitive data.
The extensions in question, both originally associated with a developer named “akshayanuonline@gmail.com” (BuildMelon), are listed below –
QuickLens – Search Screen with
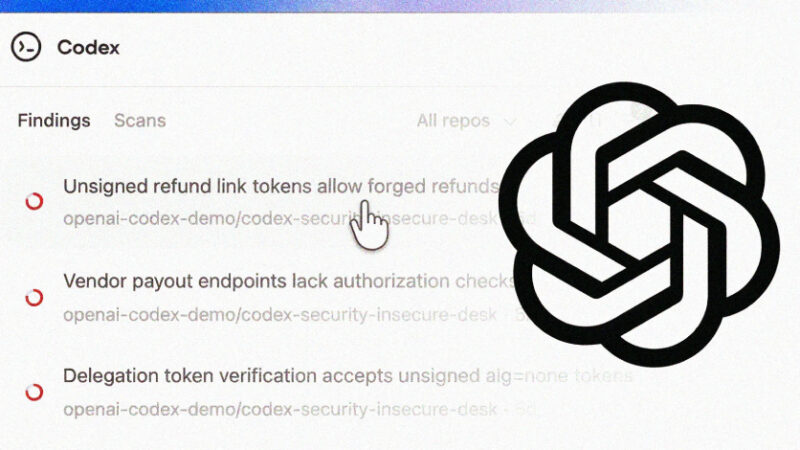
OpenAI Codex Security Scanned 1.2 Million Commits and Found 10,561 High-Severity Issues
OpenAI on Friday began rolling out Codex Security, an artificial intelligence (AI)-powered security agent that’s designed to find, validate, and propose fixes for vulnerabilities.
The feature is available in a research preview to ChatGPT Pro, Enterprise, Business, and Edu customers via the Codex web with free usage for the next month.
“It builds deep context about your project to identify